Asset Discovery
Automate the discovery process of every internet-facing asset from web apps, mobile apps, APIs and cloud.
Automated Discovery
Data Theorem automates the discovery process of every internet-facing asset and exposure and raising your overall security posture. By maintaining consistent visibility into the entire AppSec stack, Data Theorem provides a current, accurate inventory of assets and the ability to investigate assets at the individual level, or to leverage a big-picture view of your stack as a whole.
This automated visibility of all assets helps teams:
- Establish a holistic view of all application security assets, including domains, web and mobile applications, certificates, network services, hosts, cloud apps, and more.
- Provide a clear and actionable understanding of the ways that mobile and web applications connect with APIs and cloud assets.
- Scan enterprise-scale application environments quickly to identify new or shadow assets as soon as they appear.
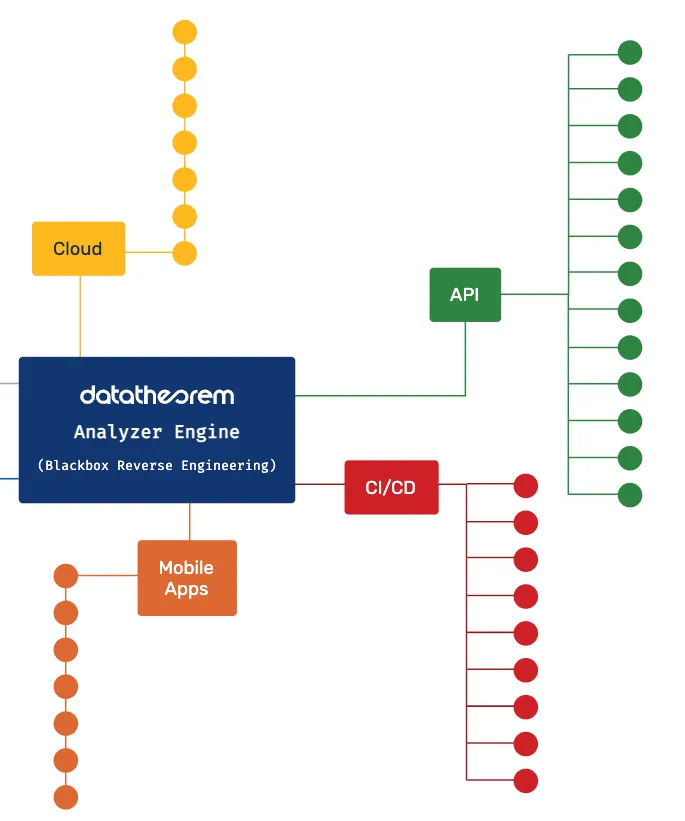
Continuous Inventory
Data Theorem products run continuous inventory and scanning - whether it be for mobile or web on the client end, APIs used to transmit information and requests, or cloud assets. There are constant scans that will reveal any new attack vectors.
In our Mobile Secure product, Data Theorem runs the discovery across all potential paths of the app where the user can interact as well as on the backend, scanning for any vulnerabilities in stored client data, linked SDKs, open source libraries, both in the binary as well as during runtime.
In our Web Secure product, the first step of the product is to expose all web apps and associated assets, particularly for single page applications that are running dynamically with 100s of linked pages on average. Data Theorem scans all the apps, private and public APIs, cloud storage assets.
WHAT ABOUT THE CLOUD?
We always connect our discovery back to the cloud. In the cloud we continue to find vulnerabilities and potential unsecured assets that are being used or linked on your front end apps for your client.
Data Theorem can run discovery on the time cadence of your choice whether it be weekly, daily, or hourly, in order to best compile your inventory. From this inventory we can then continue on to the inspection process.
Attack Surface Management
As companies expand their global and cloud footprints, security teams are seeking new solutions to discover, inspect, and remediate their greatest internet-facing risks. This helps lock in stronger visibility across all modern apps and APIs, preventing data breaches. Attack Surface Management extends beyond manual pen testing to provide a view into dangerous misconfigurations and process failures that can allow attackers easy access into cloud or web apps, or allow access to valuable data.
How we do it?
- Blackbox Discovery: No agents, configuration, or maintenance. Just continuous monitoring.
Attack Toolkits: Attack your AppSec stack just like a true adversary. - Prioritized Alerts: Separate critical alerts that need immediate attention from those that are more time consuming.
- Actionable Findings: Reporting is available 24/7 and clearly details steps to remediation.
Easy Integrations: Make it easy to collaborate, for shared visibility and ownership.
Security is mission critical for our customers. I know first-hand that no matter the size of an organization, DataTheorem can support the security challenges of any mobile application development team. Since our first mobile app deployment in 2019, our mobile development team has been extremely grateful for the efficiency of their security testing and vulnerability discovery methodology — otherwise, to write code and deploy mobile applications without DataTheorem would be like walking onto a battlefield without a helmet, flak vest, weapon, and no trench to hide in.
Prevent Data Breaches
Get Started with Data Theorem Today!
Free Trial



