Active Protection
Real-time active protection for mobile apps, web apps, APIs and cloud native-apps.
Real-time Active Protection for Apps and APIs
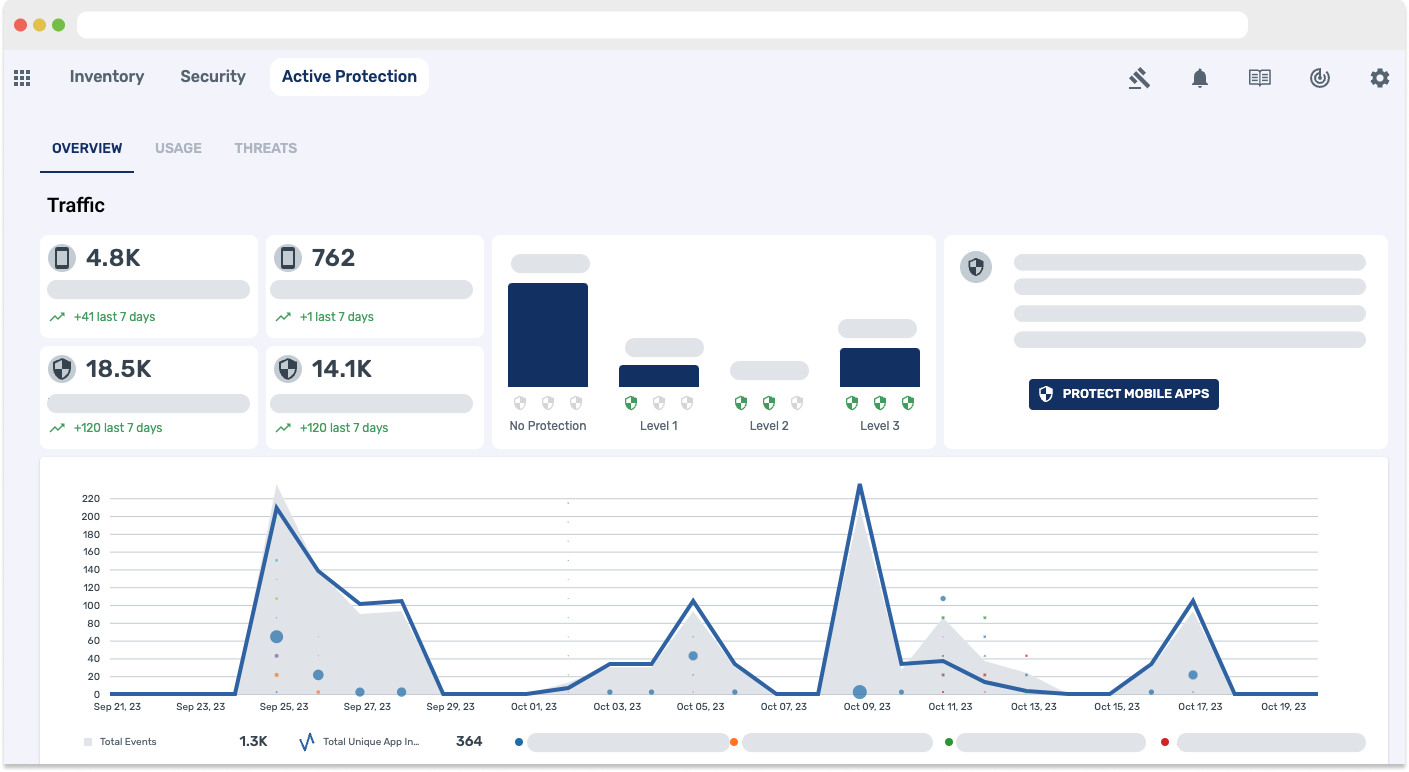
Real-time active protection for apps and APIs is a comprehensive security approach that focuses on proactively and continuously defending software applications and their associated APIs (Application Programming Interfaces) against various cyber threats and vulnerabilities in real-time. Here's a more detailed explanation of this concept:
- Continuous Monitoring: Real-time active protection involves constant surveillance and monitoring of your applications and APIs. This monitoring tracks incoming and outgoing traffic, user interactions, and data flows to identify any suspicious or unauthorized activities.
- Immediate Threat Detection: The system employs various techniques and technologies, including intrusion detection systems (IDS), machine learning, and behavioral analysis, to detect threats and vulnerabilities as they occur. It looks for signs of known attack patterns or anomalies that might indicate a security breach.
- Real-Time Response: Once a threat or anomaly is detected, the system responds in real-time to mitigate the risk. This response can include blocking malicious requests, existing the mobile app, or alerting security personnel for further investigation.
- Authentication and Authorization: Every request made to the application or API is checked for proper authentication and authorization in real-time. This ensures that only authorized users can access sensitive data or perform specific actions.
- Data Validation and Encryption: Real-time protection systems validate data inputs to prevent common vulnerabilities like SQL injection or cross-site scripting (XSS). They also ensure that data is transmitted securely using encryption, safeguarding it from interception during transit.
- Threat Intelligence Integration: These systems often incorporate threat intelligence feeds, which provide information about emerging threats and known attack patterns. By staying updated with the latest threat information, the system can better defend against evolving security risks.
Prevent Data Breaches
Get Started with Data Theorem Today!
Learn More




