2024 Market Guide for API Protection
Analyst Report by Gartner
2024 Market Guide for API Protection
The average API breach leads to at least 10 times more leaked data than the average security breach.
According to Gartner®, “Cybersecurity attacks that use APIs as an attack vector constitute a major threat to organizations and their sensitive data. This Market Guide can help security and risk management leaders understand which specialized products can assist in securing their organization’s APIs, and how.”*
We believe this report will help you understand the following:
- APIs (especially shadow and dormant ones) are causing data breaches.
- Security leaders require additional capabilities to protect their APIs.
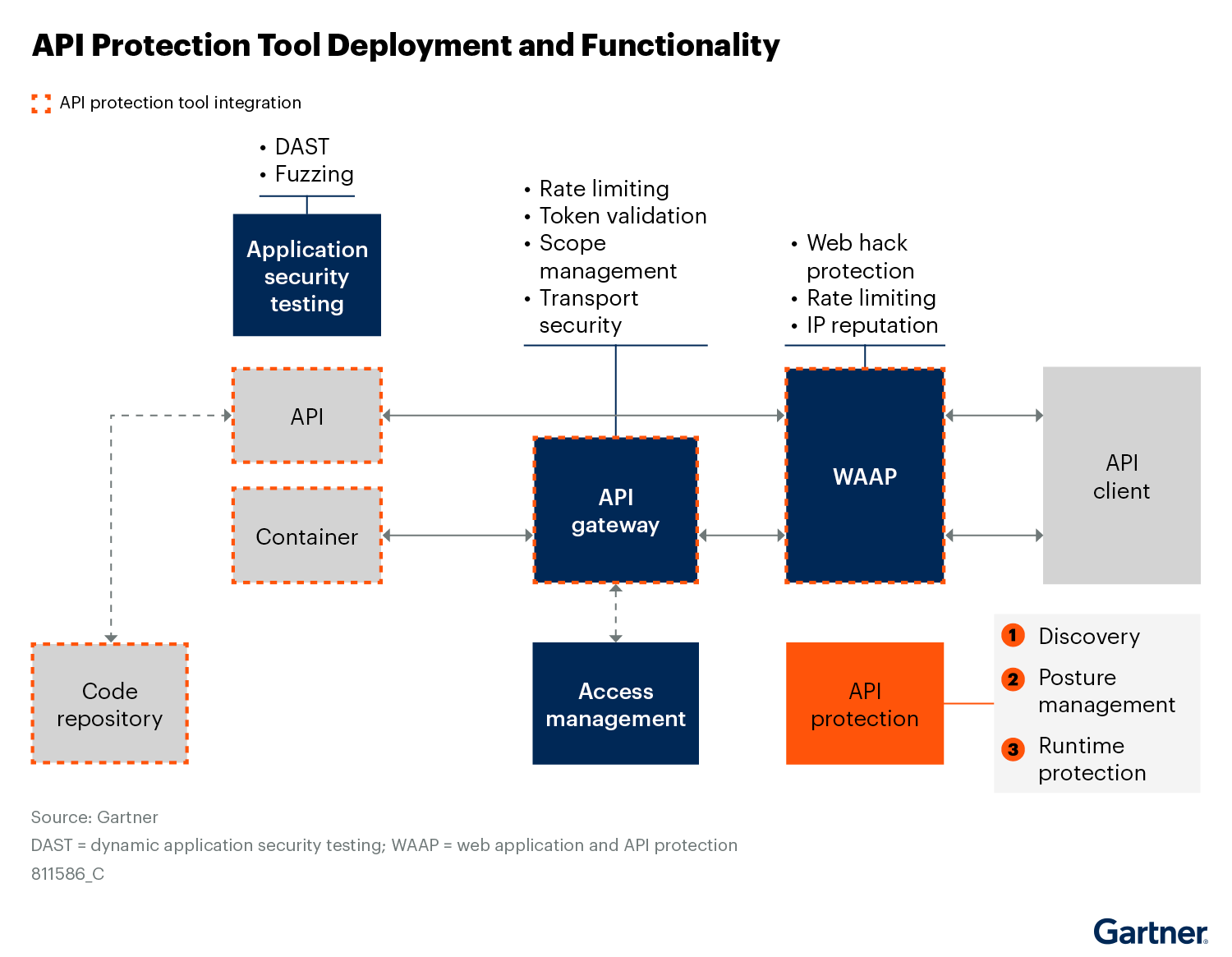
- API protection products provide discovery, posture mgmt and runtime protection.
- Continuous posture mgmt over the inventoried APIs to find and fix exposures.
*2024 Market Guide for API Protection, Dionisio Zumerle, Aaron Lord, Esraa ElTahawy, Mark O'Neill, 29 May 2024
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.
Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of opinions of Gartner's research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose