CNAPP
Cloud Native Application Protection Platform
What is CNAPP
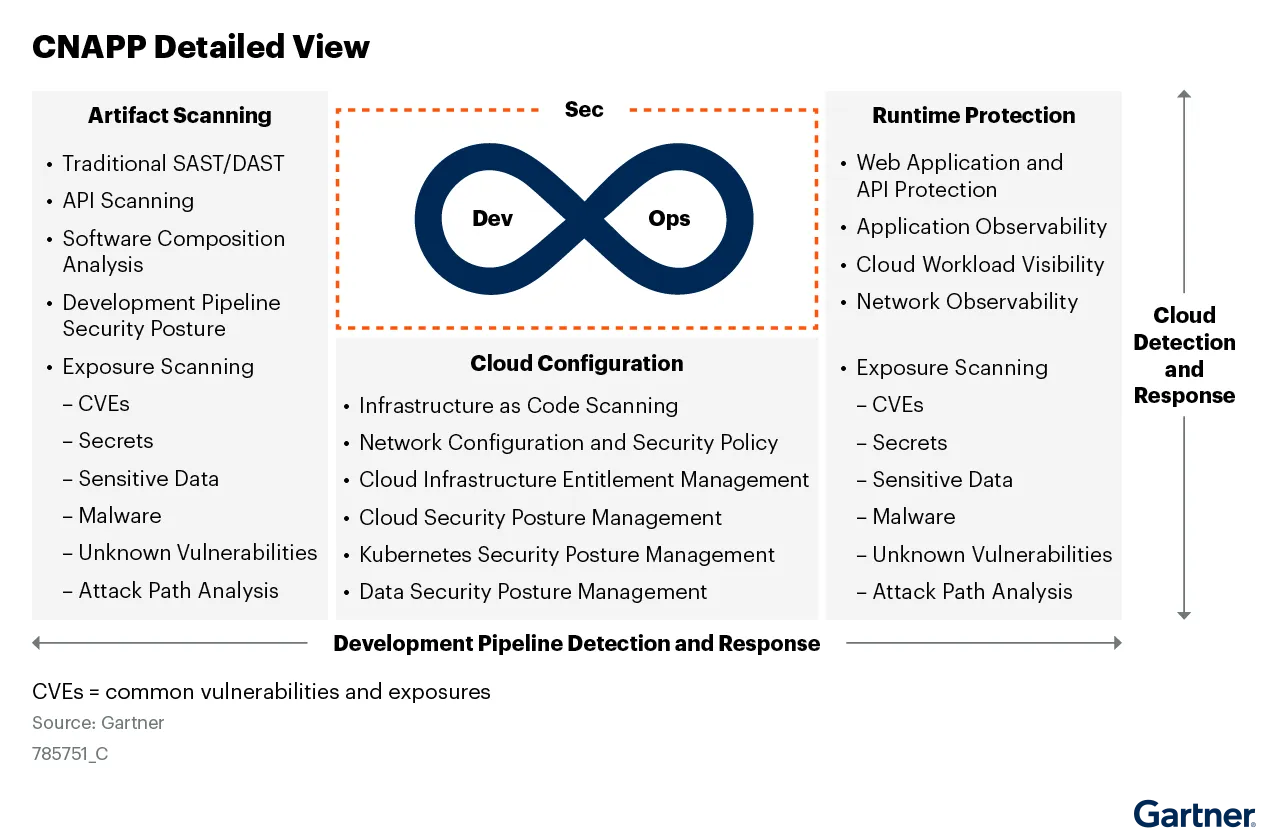
Cloud-Native Application Protection Platforms (CNAPP) address the full life cycle protection requirements of cloud-native applications from development to production. CNAPP offerings bring together multiple disparate security and protection capabilities into a single platform focused on identifying and prioritizing excessive risk of the entire cloud-native application and its associated infrastructure. The three pillars of CNAPP are:
- Artifact Scanning (DevSecOps)
- Cloud Configurations (Posture Management)
- Runtime Protection (Observability)
Data Theorem puts the APP in CNAPP
The majority of CNAPP vendors have come from two primary IT infrastructure tooling backgrounds:
- Runtime-centric using agent and firewalls.
- Cloud security posture management (CSPM).
Data Theorem uniquely stands alone with the most application-centric approach to helping customers with their CNAPP programs. Data Theorem's award-winning Analyzer Engine focuses on the full-stack of cloud-native applications that allow its Cloud Secure product to have unique attack path analysis of APIs, software supply chains, mobile, and web applications that sit atop cloud services. As a result, Data Theorem helps its customer monitor, hack, and protect their attack surfaces within their cloud-native applications often missed by traditional infrastructure security tools.
Artifact Scanning
Artifact scanning is a foundational security capability within any DevSecOps team. DevOps engineers often make incremental updates on a daily/weekly basis and the artifact scans must look for known vulnerabilities and exploits. Low false-positive rates are paramount to any useful artifact scanner. The coverage areas (languages and repositories) and application security testing capabilities are equally important. The true success metric is not in identifying problems but fixing them before they are exploited in production.
Cloud Configs and Posture Management
Cloud configurations deviating from security best-practices (defaults) are often blamed for several high-profile data breaches in the cloud. Today, cloud security posture management (CSPM) is an essential commodity but other xSPM such as Applications (ASPM) and Kubernetes (KSPM) for containers have become important factors too. Infrastructure as Code (IaC) and Cloud Infrastructure and Entitlment Management (CIEM) all fall under this category of hardening cloud configurations from a security standpoint.
Runtime Protection
Runtime observability into cloud-native workloads is often the first step toward protection. Understanding and visualizing real-world cloud abuses helps security teams better prepare and prevent attacks on their applications, APIs, and cloud resources. Some protection methods include agents, proxies, and firewalls. Other protection methods are agentless and use techniques like software development kits (SDKs) that are embedded into the applications themselves.
The attack surface of cloud-native applications is increasing. Attackers are targeting the misconfiguration of cloud infrastructure (network, compute, storage, identities and permissions), APIs and the software supply chain itself. CNAPP offerings bring together multiple disparate security and protection capabilities into a single platform focused on identifying and prioritizing excessive risk of the entire cloud-native application and its associated infrastructure.
Prevent Data Breaches
Get Started with Data Theorem Today!
Learn More




