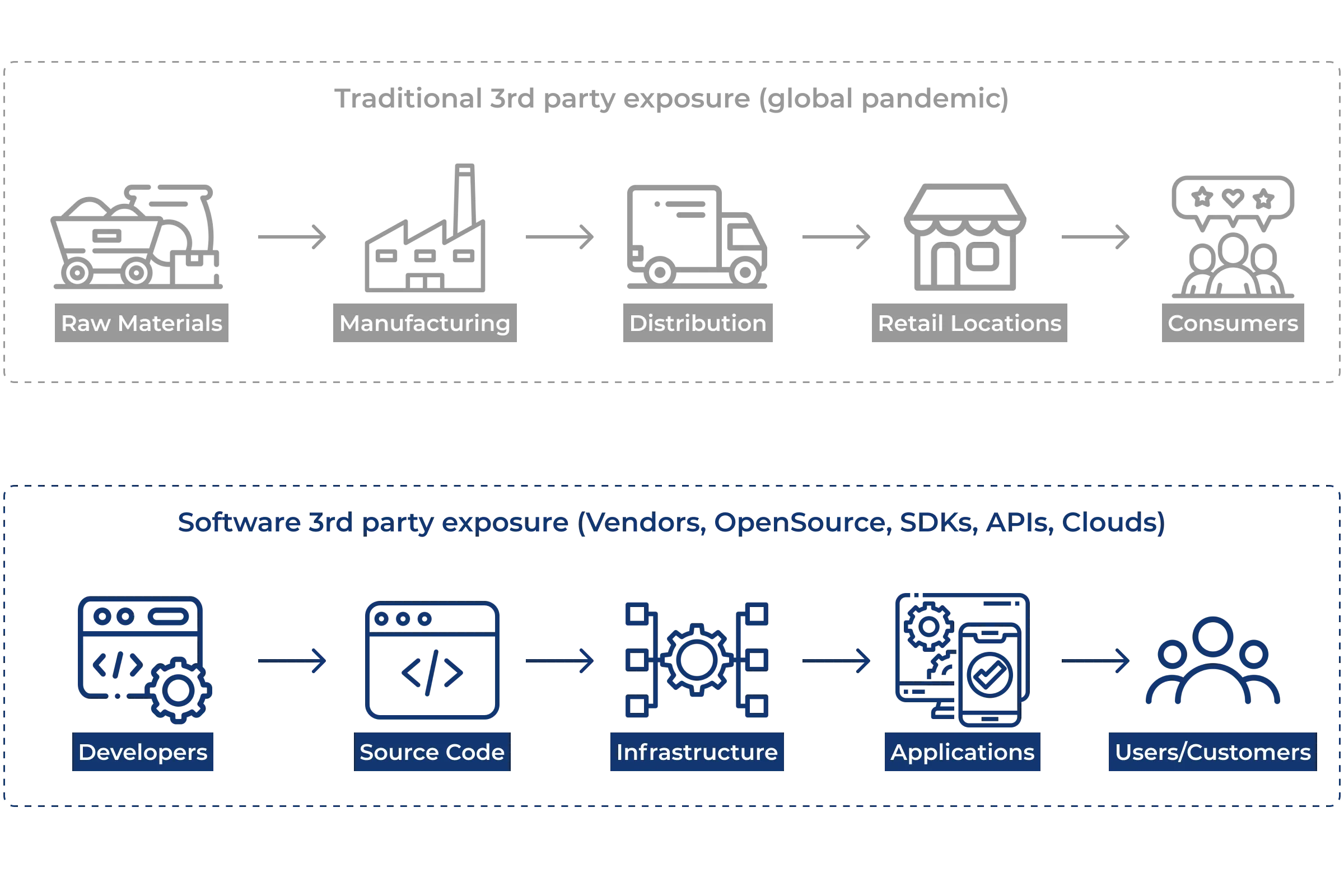
SAST, SCA and SBOM
Security violations across third party APIs, SDKs, open source libraries, and software bill of materials (SBOMs) from vendors and partners.
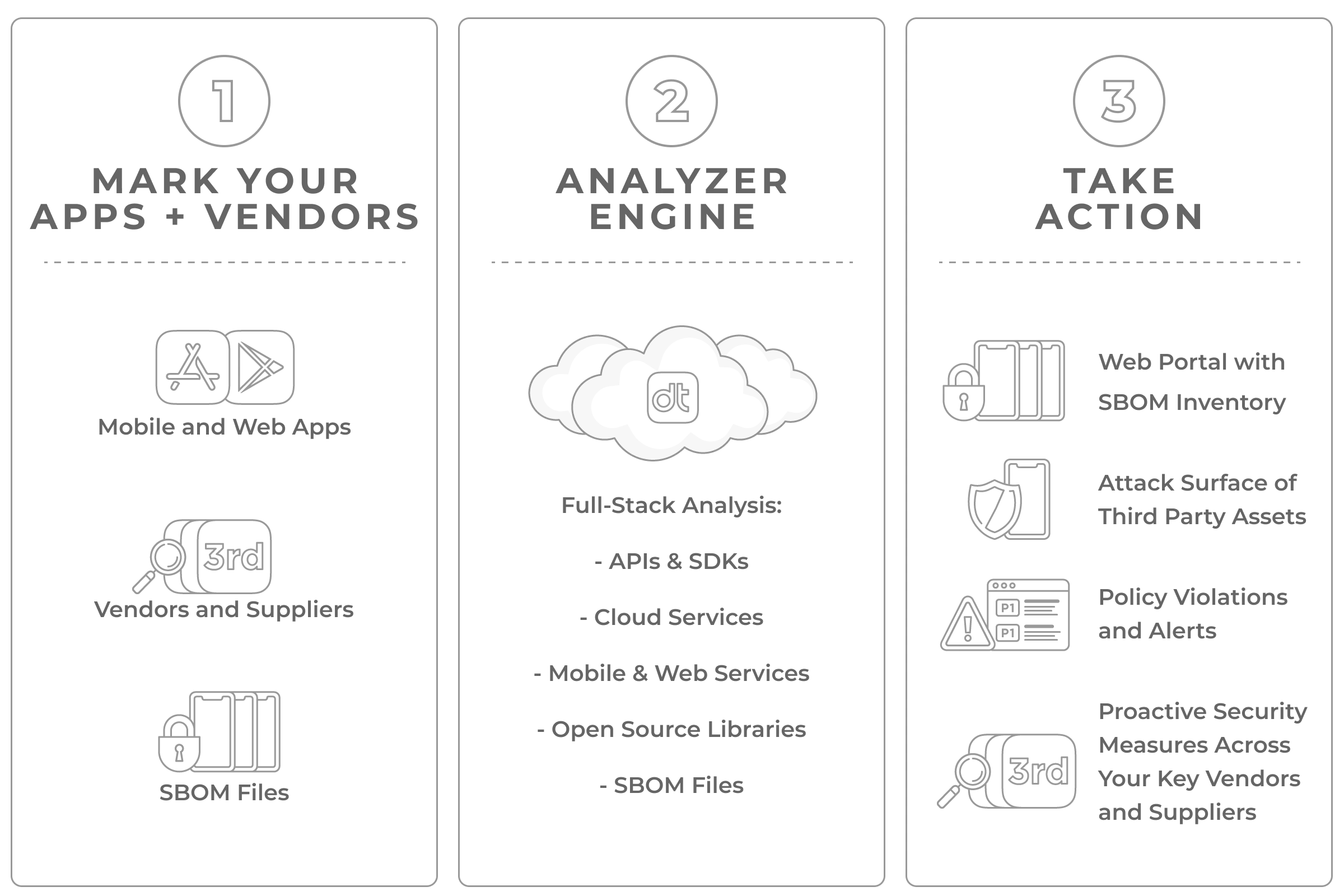
Discover Your Software Supply Chain
- Begin by marking your most important mobile and web apps (first party) and your third-party vendors and suppliers. Upload your SBOM files for ingestion.
- The Analyzer Engine will conduct full-stack analysis across first and third party APIs, cloud services, SDKs, and open sources libraries.
- Take action by identifying third party supply chain attack surfaces within your applications, opening policy violations, and listing your SBOM inventories. Create alerts on proactive security measures that your vendors and suppliers may or may not have in place.
Hack Your Supply Chain
Supply Chain security goes beyond the code with focuses across the entire application stack:
- Discover all of your 3rd Party assets:
- APIs, SDKs, Open Source
- Cloud, Mobile, Web Services
- Hack 3rd Party Attack Surfaces
- Automate Vendor Management
- Ingest software bill of materials (SBOM) files
- Create dynamic SBOM inventory listings based on full-stack analysis
The analyzer engine discovers third-party assets across the application full-stack using runtime analysis (dynamic, interactive security testing)
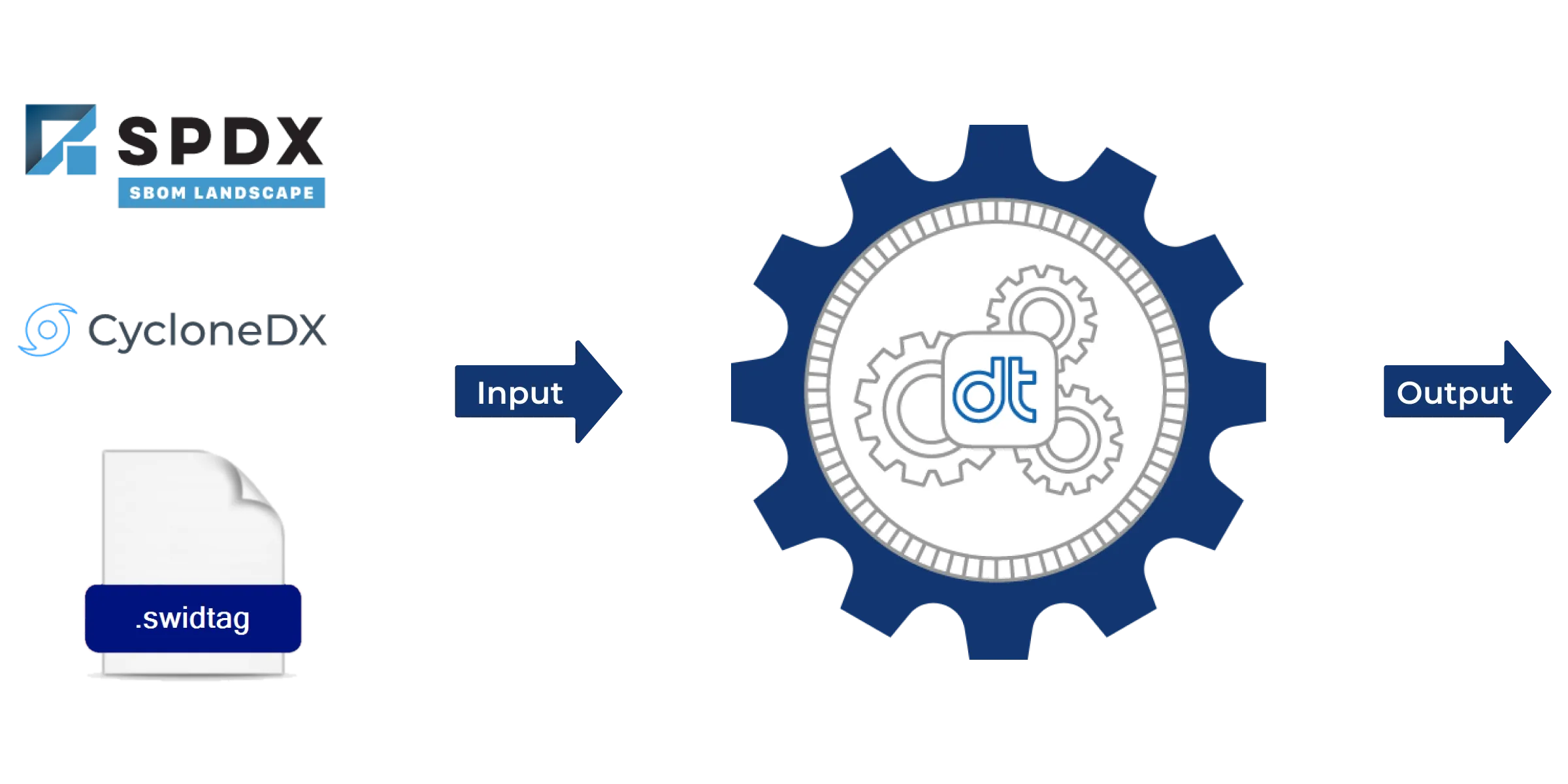
Manage SBOM Inventory
Data Theorem’s Code Secure allows customers to ingest all of their SBOM files to be processed by its Analyzer Engine. As an output, Data Theorem's Code Secure pipeline will generate a comprehensive SBOM Inventory listing based on multiple sources including SBOM files and full-stack application analysis.
SBOM is defined as a “formal record containing the details and supply chain relationships of various components used in building software. Software developers and vendors often create products by assembling existing open source and commercial software components. The SBOM enumerates these components in a product. It is analogous to a list of ingredients on food packaging.”
Executive Order on Improving the Nation’s Cybersecurity, May 2021
We look forward to Data Theorem’s continued push into API, Web, and Cloud security to give us security visibility into our entire stack.
Prevent Data Breaches
Get Started with Data Theorem Today!
Learn More